4 Inconvenient but Effective Security Measures
Security usually requires sacrificing convenience (or money). So naturally, we tend to get away with as little security as possible. But if you’re a glutton for punishment, here are 4 very inconvenient but highly effective measures you can take right now to protect yourself from the evils lurking on the interwebs.
Disable JavaScript
Yeah, I know. Every site made since the Web 2.0 days needs JavaScript just for a text input field to work right. It’s a shame, really. But disabling JavaScript isn’t an all-or-nothing deal. Browser extensions lets you allow JavaScript for sites you trust and block them for all others. If you’re still using Firefox (the most obnoxious browser today), you can use the NoScript extension. Chrome users, check out uMatrix.
Disable XSS
Cross-site scripting (XSS) occurs when you go to one website and it loads JavaScript from a different domain. Sadly, this practice has become normal with the advent of CDNs. What makes it risky is not so much the cross-site request, but the fact that it happens without you knowing it. You don’t see that legitwebsite.com is loading Nasty.js from someone’s hijacked blog site. Using one of the script blocking extensions I just mentioned will warn you about XSS and let you decide whether to allow it. I’ve stopped several malicious scripts this way over the years.
Block wide categories of websites
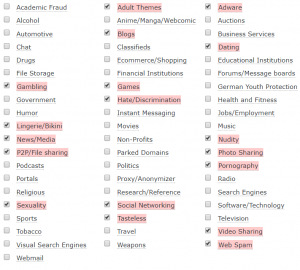
Taking a whitelist approach is too inconvenient, as there are just way too many sites out there to keep up with. Your next best option is to use content-based filtering to block websites by category. I use OpenDNS to achieve this, and below is my current list of blocked categories. As you can see, it’s pretty broad.
This list covers some sites I don’t want blocked, so I allow those on a case-by-case basis. You might notice that some of these categories tend to carry malware more than others, so blocking them wholesale is a pretty effective way to avoid fallout from clicking the wrong link.
Don’t use the app
Smartphones normalized a concept that would’ve been considered bizarre just a few years ago: installing an app for every website you use regularly. We’ve got Twitter, Facebook, Gmail, LinkedIn, etc. Can you imagine installing “the MySpace app” on your Windows XP machine in 2005? Some sites just don’t need an app. You can browse to them on your phone and they work fine.
When you install an app, you usually give it permissions to various system resources – photos, call logs, camera, microphone, etc. Chances are the core functionality doesn’t require most of those. If that app has a vulnerability – or worse, malicious code – then you’ve just turned your phone into a neat little hacker toolkit.